
Let be begin by saying: Selectively blocking Javascript is essential for online privacy.
Fundamental idea
- Javascript is needed for way too many websites to load correctly
- Websites often dont only use their own Javascript to display their own menus etc. but they load tons of external Javascript.
- There is often way more Javascript that you can block than what you need
- No “privacy browser” can protect you if you dont invest the work of blocking Javascript per origin
- there are many origins that just serve bullsh*t so you can always block them
- browser sandboxes, process isolation etc. is only needed because of Javascript or CSS exploits
- there are hacks that work through CSS only, but they are rare
- this is why browser isolate every website in a process. They isolate these processes from the system with strict filters and sandboxes
Sum up
Javascript is a technology used to display fancy websites, moving parts, responsive interfaces etc.
It is executed code, in your browser. Unlike normal applications, the code comes from random places on the internet, and is often malicious.
This is why browsers need to be so secure.
Many developers bundle random 3rd party javascript into their website, mostly for capitalist “get some more cents” purposes.
This is what a shitty website looks like (and yes it runs perfectly fine after blocking all that)
This means often: the website, AND the developers of the javascript will both get your personal data.
If you block Javascript, you avoid 99% of security issues, and automatically block most trackers.
Websites cannot place cookies in the browser, if you block javascript!
Some things to know
- Google reCaptcha is a nasty difference, as it requires many origins at once. NoScript has the “allow all Javascript on this tab” for this purpose
- some sites may load fine without Javascript, but menus dont work.
Setup of NoScript
Install the Addon and go into its settings.
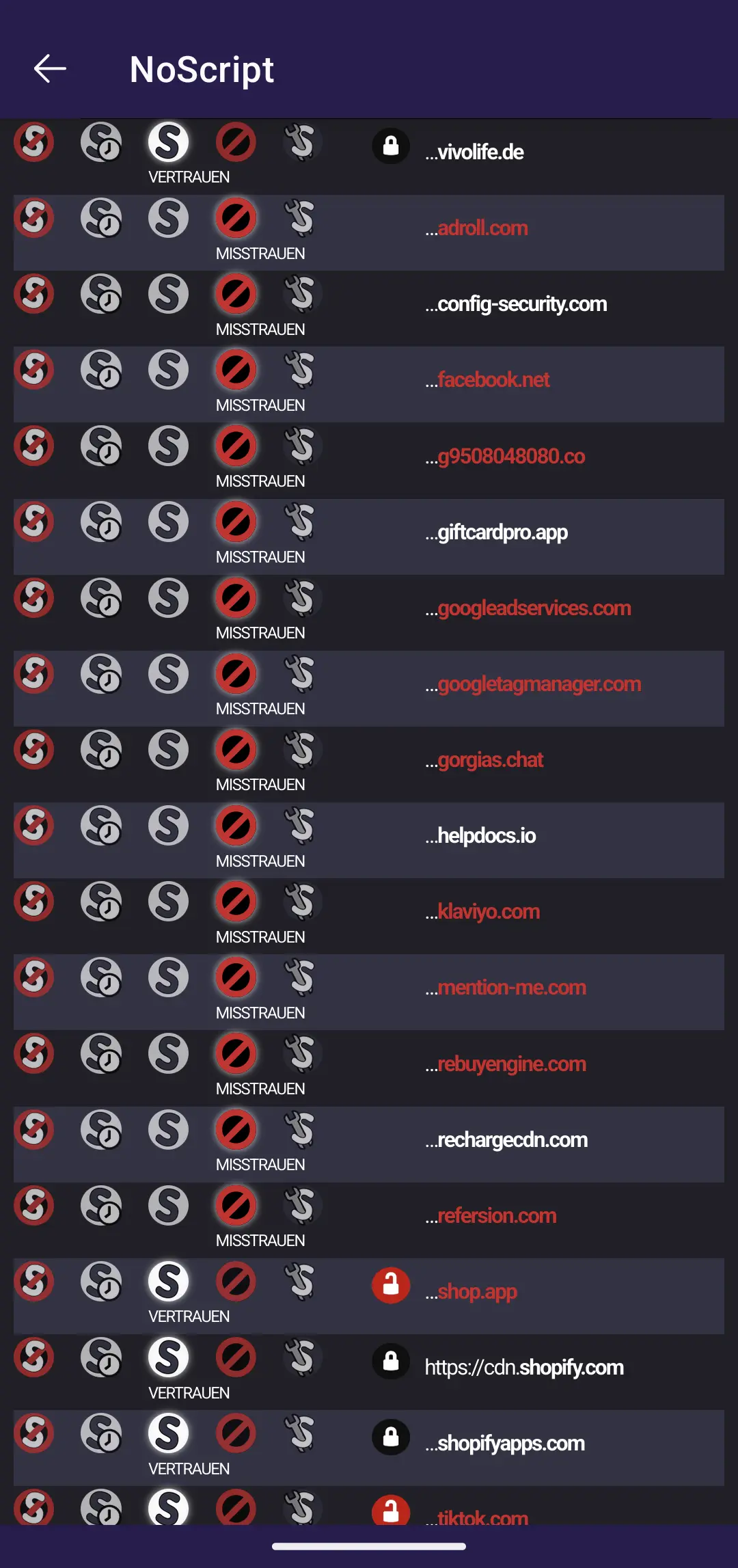
per site permissions
It has some very loose, “security only” settings, so most of “Big Tech” is trusted by default. If you dont use it, set it to “untrusted”.
general settings
Here you can select what “default”, “trusted” and “untrusted” do.
Default
- I change it to “block all”. Most websites dont load with the default settings anyways
- if you set “noscript”, websites can see that “your browser does not support Javascript”. This may cause them to display a no-js website, but that is really rare.
- The “noscript” makes you stand out from the crowd very likely. There are other methods to check if you support javascript, like just trying to run it.
Trusted
- I enable everything but these:
ping: pretty shady stuff, thanks @leanleft@lemmy.mlnoscript: you support Javascript so not usefulLAN: block requests to your local network, should not be needed in most casesunverified CSS: important blocking this is more secure (see above, CSS-only exploits are possible) but drastically slows down the speed of your browserother: better not enable random other Javascript types
Untrusted
- block everything
- maybe allow
noscript(see above)
See the explanations for all Javascript variants here
Workflow of NoScript
I think the author didnt really consider the implications, so these loose settings make little sense.
NoScript makes most sense for “goodness enumeration”. By default, all Javascript is blocked.
At the beginning it may be annoying, but it will become less and less work:
- Open a website
- It likely doesnt load
- Click on the NoScript icon
- Set the Javascript of this Website to “trusted”
- NoScript automatically reloads the site
- maybe: Repeat, you may need to allow CDNs, image hosts etc.
Once you did this to all your commonly visited sites, only new ones will need manual configuration.
This approach becomes less effort over time, unlike badness enumeration, which gets more and more.
(I thought about giving you my 2 years old configuration as a headstart, but it is basically my browsing history. I would be interested in sharing a config on some Git host though, as this makes starting with NoScript way more pleasant)
Background on “badness enumeration”
Adblockers use something called “badness enumeration”.
Example of badness enumeration:
- Adblockers: allow all content to load, block a, b and c ONLY
- Malware scanners: allow all code to execute, but block hashes a, b, c
- Some Firewall Blocklists: allow all incoming traffic, but block all IPs coming from Russia
The system is fundamentally flawed, as
- The authors of blocklists always need to be perfectly up to date
- Once a new malware/site/ad comes out, it will stay unblocked for a while
- It assumes every user needs the same
- It needs always growing filterlists and malware databases, that get bigger and bigger
Avoid badness enumeration when possible. Btw, NoScript likely also blocks many Ads on websites.


I’m still using uMatrix (actually a nuTensor fork) because of other features. uBO doesn’t have the exact same features…
is it possible to block XSS requests and enable cookies for selected domains on NoScript as well?
Will look at nuTensor!
XSS requests show a popup and I think you can say “allow always” there. Cookies are not that dangerous if you delete them on close. I mean there are people that never shut down their PCs… but yeah.